Defense Tools
Defensive strategies for protecting your organization from Google Hacking attacks traditionally have been limited. Most fall back on the approach of “Google Hack yourself,” which has several shortcomings. While a few free tools exist that allow security staff to Google Hack their organization, they are typically inconvenient, only utilize one search engine and provide a tiny snapshot of your organization’s exposure.
Bishop Fox has created the first-ever truly defensive tools to help protect your organization from exposed vulnerabilities via Google, Bing and other popular search engines. These tools are comprised of two major types: Alert RSS Feeds and Alert RSS Monitoring Tools. Together, they form a type of intrusion detection system (IDS) for Google hacking.
Note (17Aug2013) – Google Reader has been shut down as of 01July2013, and consequently Google Alerts has temporarily suspended its RSS delivery capabilities. This has caused the Diggity Alerts FUNdle Bundle and other Google Alert based feeds to stop working for the time being.
The Bing and SHODAN engine based RSS alerts are still working at the moment. We will continue to monitor the situation and look for a working alternative to re-enable the Google RSS alerts.
Alert RSS Feeds
Diggity Alerts FUNdle Bundle
 Utilizes Google Reader Bundles to combine all of the Diggity Alert feeds (e.g. Google Hacking Alerts, Bing Hacking Alerts, …) into a single RSS feed.
Utilizes Google Reader Bundles to combine all of the Diggity Alert feeds (e.g. Google Hacking Alerts, Bing Hacking Alerts, …) into a single RSS feed.
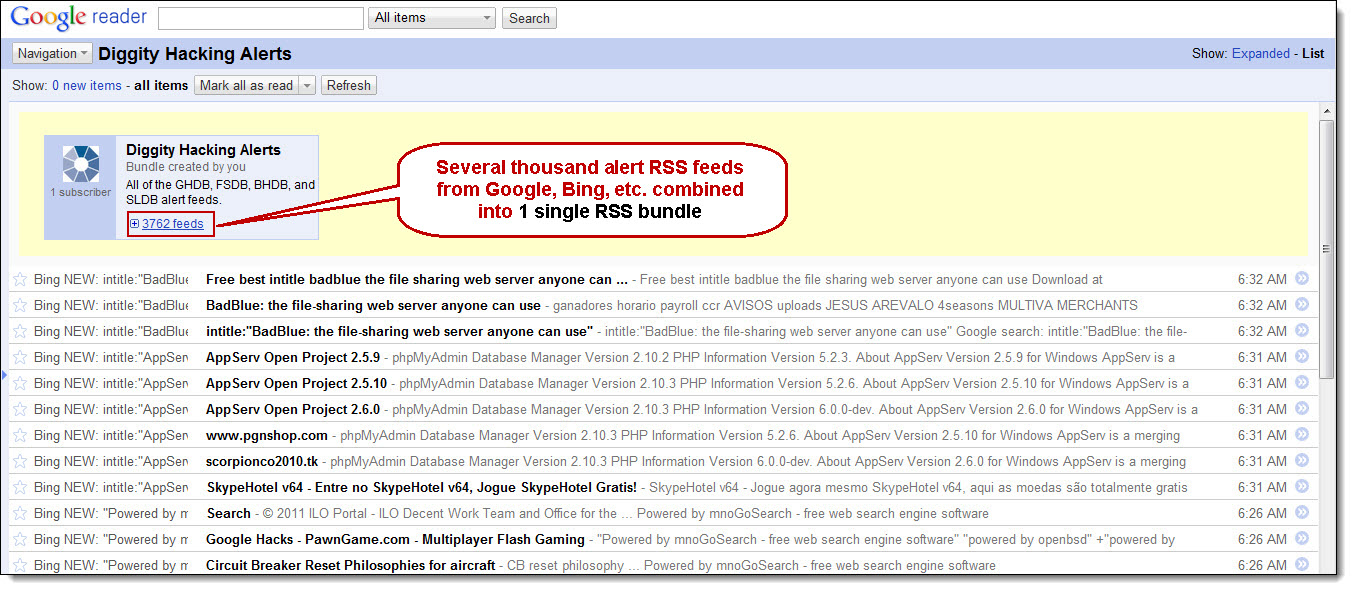
Google Hacking Alerts
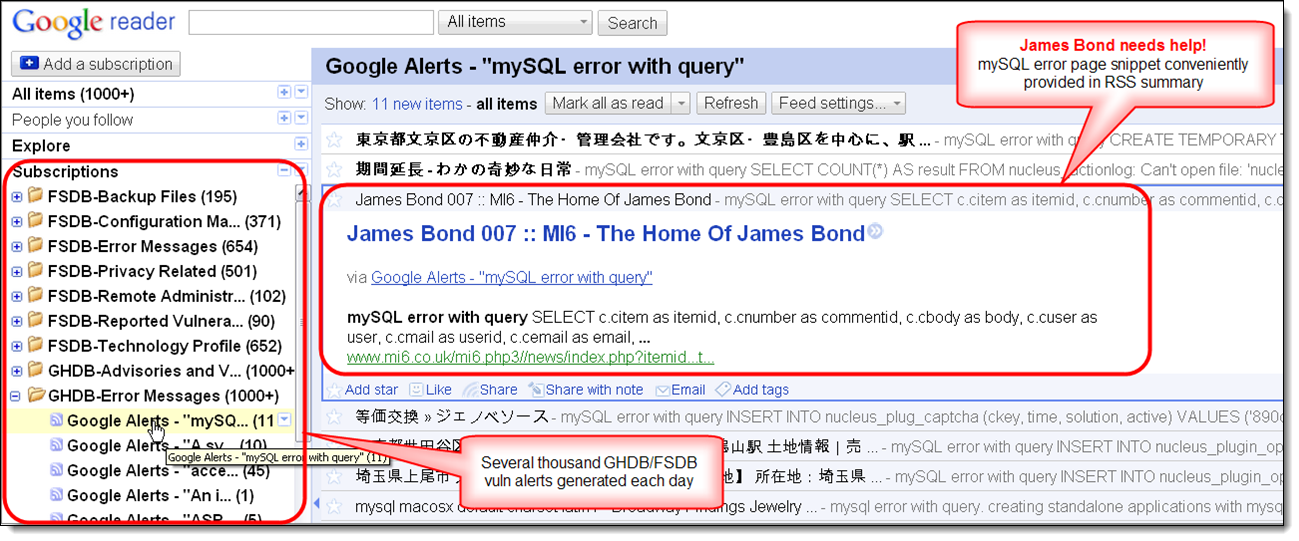
Google Hacking Alerts provide real-time vulnerability updates via convenient RSS feeds. Google Alerts have been created for all 1623 GHDB/FSDB search strings, which generate a new alert each time newly indexed pages by Google match one of those regular expressions.
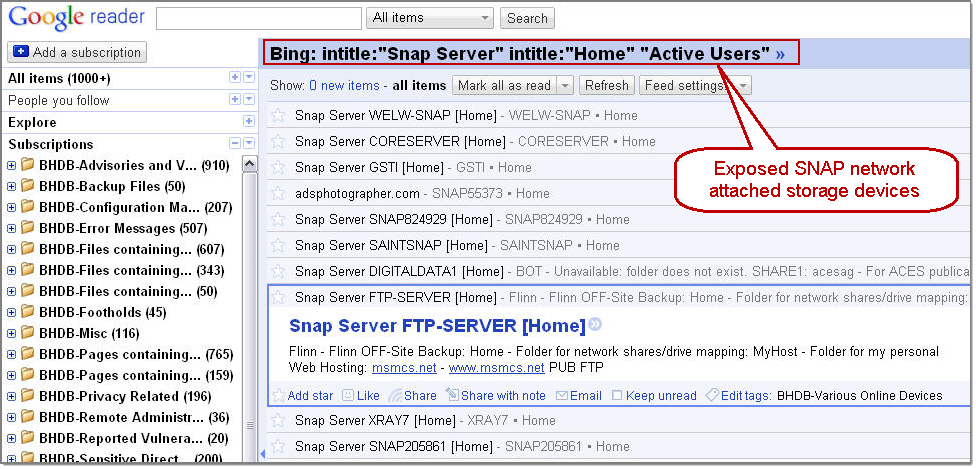
Bing Hacking Alerts
Bing Hacking Alerts employs a similar approach, but instead leverages Bishop Fox’s Bing Hacking Database (BHDB) in conjunction with Microsoft Bing’s &format=rss directive to turn Bing searches into RSS feeds.
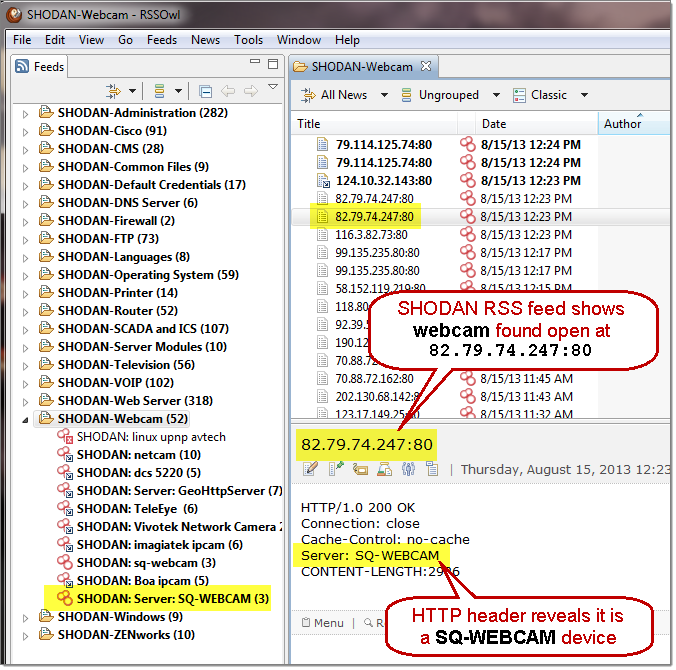
SHODAN Hacking Alerts
 New, live vulnerability RSS feeds based on results from the popular SHODAN hacking search engine.
New, live vulnerability RSS feeds based on results from the popular SHODAN hacking search engine.
SHODAN is a search engine that lets you find specific types of computers (routers, servers, etc.) using a variety of filters. Some have also described it as a search engine of service banners. SHODAN collects data mostly on web servers at the moment (port 80), but there is also some data from FTP (21), SSH (22) Telnet (23), SNMP (161) and SIP (5060) services.
Web search engines, such as Google and Bing, are great for finding websites. But what if you’re interested in finding computers running a certain piece of software (such as Apache)? Or you want to see how many anonymous FTP servers there are? Maybe a new vulnerability came out and you want to see how many hosts it could infect? Traditional web search engines don’t let you answer those questions.
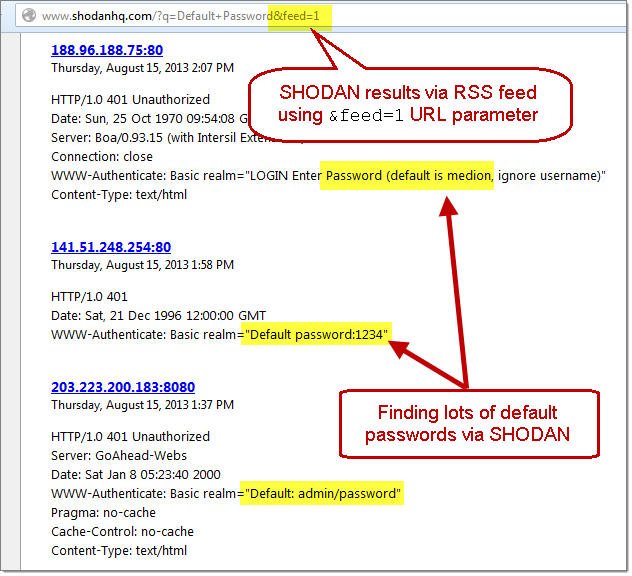
Bishop Fox incorporates SHODAN data into its defense alerts by utilizing the feature to turn SHODAN search results into RSS feeds by appending &feed=1 to common SHODAN query URLs. As an example: http://www.shodanhq.com/?q=Default+Password&feed=1
Alert RSS Monitoring Tools
AlertDiggity - Windows Systray Application
AlertDiggity is a Windows systray application that filters the results of the various Google/Bing/SHODAN hacking alerts RSS feeds and notifies the user if any new alerts match a domain belong to them.
iDiggityAlerts - iPhone Application
iDiggityAlerts is an iPhone application that filters the results of the various Google/BingHacking Alerts RSS feeds and notifies the user if any new vulnerability alerts match a domain belonging to them.
MalwareDiggityAlerts
Leverages the Bing Search API (Windows Azure Marketplace) and the Google Safe Browsing API together to provide an answer to a simple question, “Am I being used as a platform to distribute malware to people who visit my website?”
MalwareDiggityAlerts identifies off-site links of your websites by using Bing’s linkfromdomain: search directive and then creates RSS feeds to provide real-time updates to new off-site links discovered using Bing’s &format=rss directive. Those off-site links are tested and compared to known malware distribution sites by running them against Google’s Safe Browsing API.
