Attack Tools
Sometimes, the best defense is a good offense. Bishop Fox’s attack tools for Google Hacking level the playing field by allowing our clients to find information disclosures and exposed vulnerabilities before others do. Arm yourself with our arsenal of attack tools that leverage Google, Bing, and other popular search engines.
SearchDiggity
SearchDiggity v 3
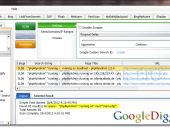
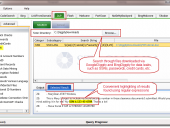
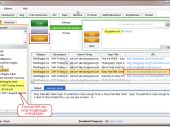
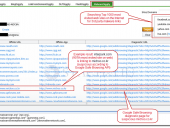
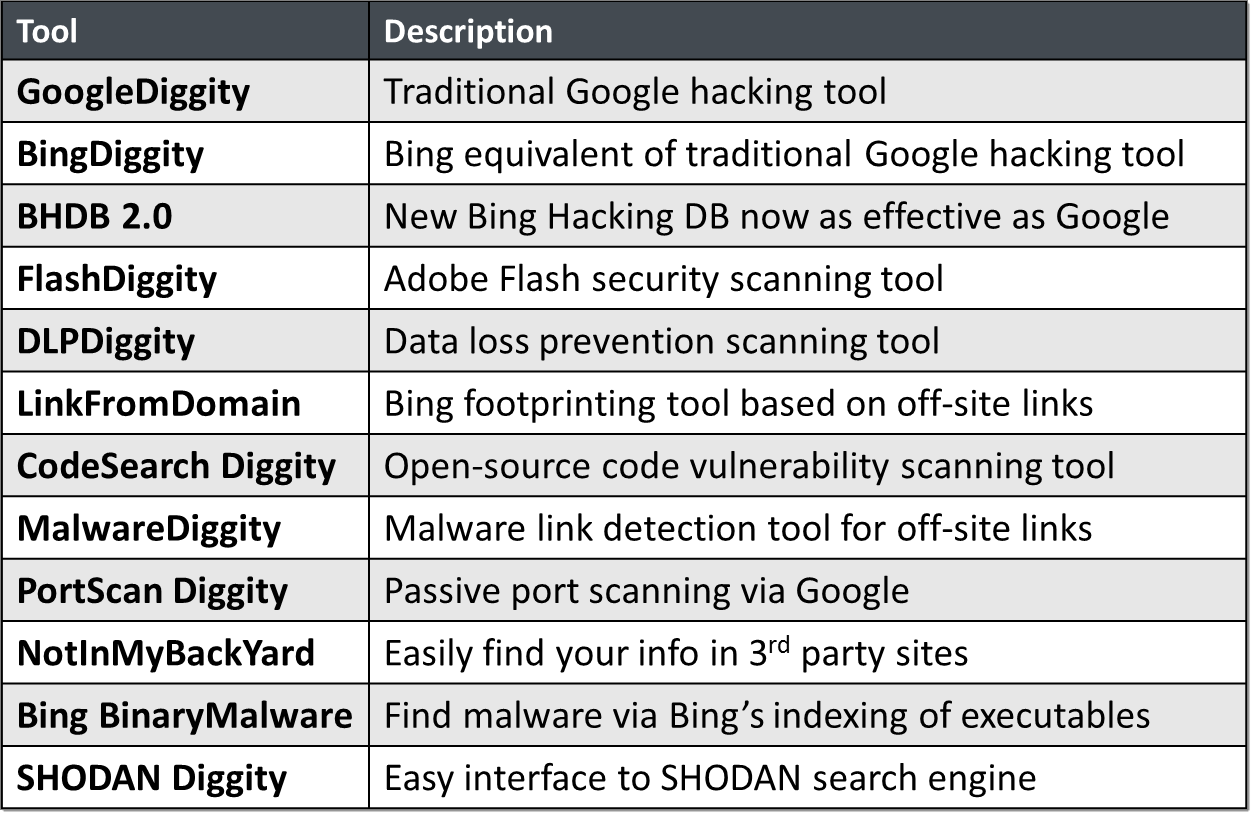
SearchDiggity 3.1 is the primary attack tool of the Google Hacking Diggity Project. It is Bishop Fox’s MS Windows GUI application that serves as a front-end to the most recent versions of our Diggity tools: GoogleDiggity, BingDiggity, Bing LinkFromDomainDiggity, CodeSearchDiggity, DLPDiggity, FlashDiggity, MalwareDiggity, PortScanDiggity, SHODANDiggity, BingBinaryMalwareSearch, and NotInMyBackYard Diggity.
Hacking Dictionaries
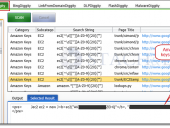
Bing Hacking Database - BHDB v2
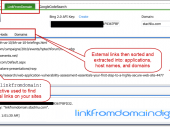
 Exploiting recent API changes and undocumented features within Bing, we’ve been able to completely overcome the previous Bing hacking limitations (such as the disabling of the inurl:, link: and linkdomain: search operators) to create an entirely new BHDB v2.0 that makes Bing hacking just as effective as Google hacking (if not more so) for uncovering vulnerabilities and data leaks on the web.
Exploiting recent API changes and undocumented features within Bing, we’ve been able to completely overcome the previous Bing hacking limitations (such as the disabling of the inurl:, link: and linkdomain: search operators) to create an entirely new BHDB v2.0 that makes Bing hacking just as effective as Google hacking (if not more so) for uncovering vulnerabilities and data leaks on the web.
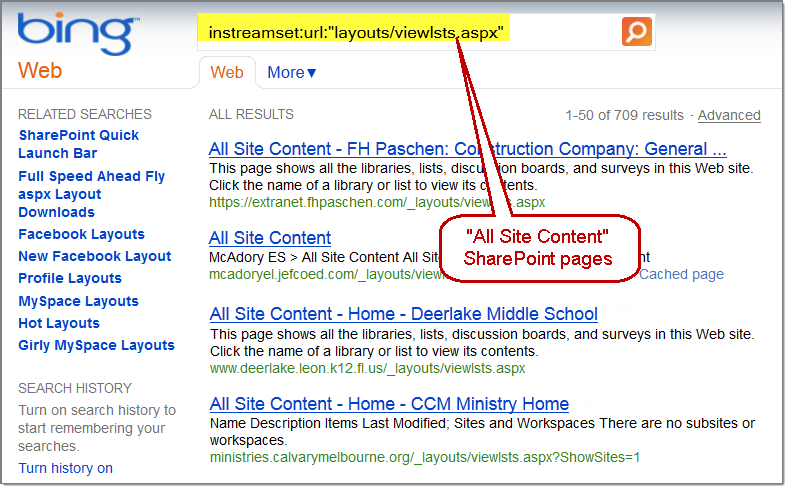
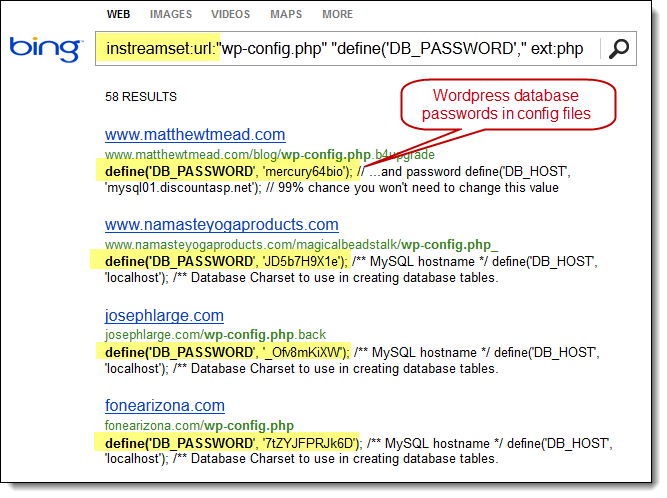
For example, Bing now has ability to use the ext: search operator, which previously didn’t exist. Bing also now has the ability to mimic Google’s inurl: search operator by using Bing’s instreamset:url: search operator.
The BHDB v2.0 also includes an entirely new SharePoint Bing Hacking database, containing attack strings targeting Microsoft SharePoint deployments via Bing.
GHDB Reborn Dictionaries - Exploit-DB
The good folks over at Exploit-DB.com were kind enough to pick up where Johnny Long left off and resurrect the GHDB. They now maintain an updated version of the GHDB in a project labeled Google Hacking Database Reborn.
In that same spirit, we at the Diggity project were kind enough to translate their efforts into GoogleDiggity compatible input text files. These dorks are included with the standard SearchDiggity dictionary set, and can also be downloaded below.
SHODAN Hacking Database - SHDB
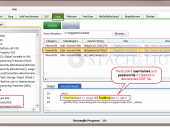
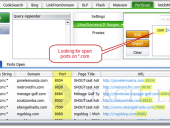
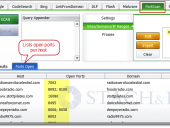
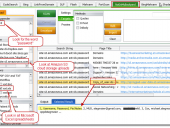
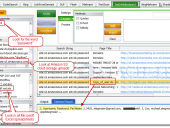
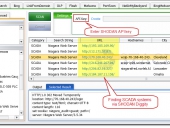
 The new SHODAN Hacking Database (SHDB) input dictionary file containing 167 queries that allow users to uncover interesting information via the SHODAN search engine. This dictionary helps target various technologies including webcams, printers, VoIP devices, routers, switches, and even SCADA/Industrial Control Systems (ICS) just to name a few. This dictionary comes preloaded with SHODAN Diggity (part of the SearchDiggity attack tool suite), which provides an easy-to-use scanning interface to the popular SHODAN hacking search engine, using the SHODAN API.
The new SHODAN Hacking Database (SHDB) input dictionary file containing 167 queries that allow users to uncover interesting information via the SHODAN search engine. This dictionary helps target various technologies including webcams, printers, VoIP devices, routers, switches, and even SCADA/Industrial Control Systems (ICS) just to name a few. This dictionary comes preloaded with SHODAN Diggity (part of the SearchDiggity attack tool suite), which provides an easy-to-use scanning interface to the popular SHODAN hacking search engine, using the SHODAN API.
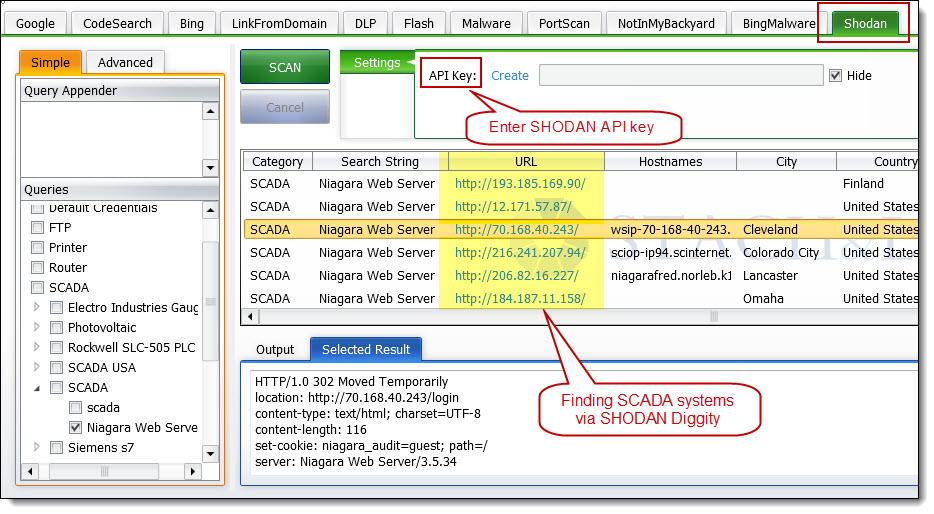
SHODAN is a search engine that lets you find specific types of computers (routers, servers, etc.) using a variety of filters. Some have also described it as a search engine of service banners. Shodan collects data mostly on web servers at the moment (port 80), but there is also some data from FTP (21), SSH (22) and Telnet (23) services.
Web search engines, such as Google and Bing, are great for finding websites. But what if you’re interested in finding computers running a certain piece of software (such as Apache)? Or you want to see how many anonymous FTP servers there are? Maybe a new vulnerability came out and you want to see how many hosts it could infect? Traditional web search engines don’t let you answer those questions.
Hacking Google Custom Search
Hacking CSE for All Top Level Domains
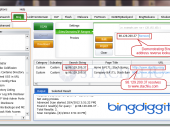
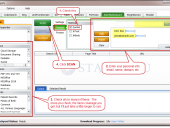
Previously, the Google Diggity hacking tools provided an extra bonus feature of allowing you to specify a Google Custom Search Engine (CSE) id to have search queries performed against a custom Google engine of your creation.
With the retirement of the Google AJAX API announced on November 1, 2010, we’ve since migrated our Google Diggity tools to the new Google JSON/ATOM Custom Search API. With this new API, utilizing Google Custom Search Engines is now a requirement, and not just a bonus add-on feature.
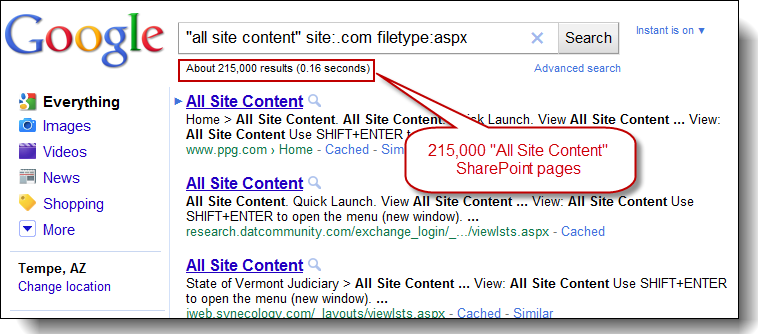
Another way to go is to use this document, which provides a quick overview of how you can create a Google CSE of your own that simulates getting the normal full results of Google (i.e. search results across the whole Internet). We accomplish this by creating a Google CSE that returns results for all top level domains (TLDs) – examples: .com, .org. .gov, .edu, …
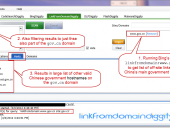
Bypassing Google CSE to get Full Web Search Results
Wouldn’t it be nice to go through the Google Custom Search API, but still get the full Google results for the entire Internet (i.e. not filtered results)? You can! Bypass using an exclamation point before any valid Google CSE id value, try: !001280586187183383443:vcqkedkugeo