Metasploit Anti-Forensics Project
The Metasploit Anti-Forensics Project, originally created by our team and now maintained by the community, seeks to develop tools and techniques for removing forensic evidence from computer systems. This project includes a number of tools, including Timestomp, Slacker, and SAM Juicer, many of which have been integrated in the Metasploit Framework.
Downloads currently unavailable
Metasploit Anti-Forensics Project Tools
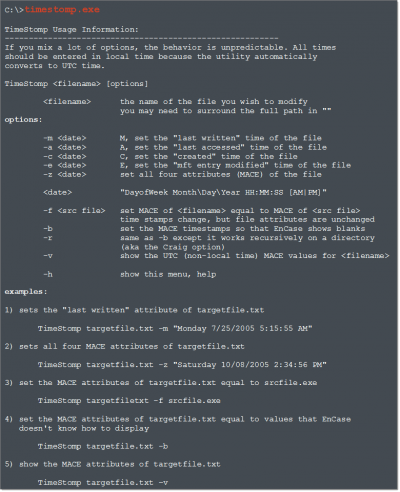
Timestomp
Timestomp allows you to delete or modify all four New Technology File System (NTFS) timestamp values: Modified, Accessed, Created and Entry Modified.
Downloads currently unavailable
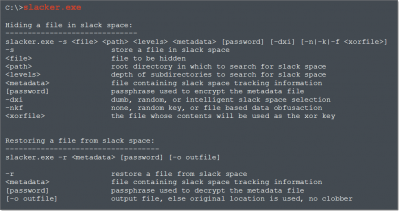
Slacker
Slacker allows you to hide data in the slack space of NTFS. This slack space is created when a file system allocates space for a file to be written, it will typically allocate more space than it actually uses. The unused space is called slack space and perfect data-hiding grounds for the hacker.
Downloads currently unavailable
Sam Juicer
The Sam Juicer runs over a memory/LSASS channel to dump password hashes on a Windows system without leaving any sort of trace or signature on the disk or registry.
Downloads currently unavailable
Metasploit Anti-Forensics Project Advisories
PGP Desktop Wipe Free Space Flaw
December 8, 2005
PGP Desktop includes a Wipe Free Space utility that claims to eliminate data in all the free space on your hard drive including the little areas after the end of existing files which may still have old data left behind. In short, the utility claims to wipe file slack space, the unused space in a disk cluster. The software does not work as advertised. It does not clean slack space.
Windows File Time Stamp Display Flaw
December 7, 2005
Windows file time stamps can be set to extremely low values via the NtSetInformationFile() system call. The Windows API does not properly translate the low 64-bit time values stored on disk into human readable format, and displays no information instead. Although this is not a security vulnerability in itself, it adversely affects third-party applications that rely upon the Windows API to perform the translation.
Metasploit Anti-Forensics Project Conferences
Conference Slides
Our presentation slides from speaking at conferences on research related to this tool project.
Downloads
Conference Videos
Black Hat USA 2005 – Catch Me If You Can – 27July2005:
Metasploit Anti-Forensics Project Documents
Articles
Articles discussing research related to this tool project.