Attack Tools
Sometimes, the best defense is a good offense. Bishop Fox’s attack tools help SharePoint administrators and security professionals identify common insecure configurations and exposures introduced by vulnerable SharePoint deployments.
SharePoint Tools
SharePointURLBrute
SharePointURLBrute is a new SharePoint hacking utility developed to help assessors quickly test user access to 101 common SharePoint administrative pages (e.g. “Add Users” page -> /_layouts/aclinv.aspx) by automating forceful browsing attacks.
This command line tool is a must have for anyone assessing Microsoft SharePoint deployment(s), enabling you to quickly identify holes in user access permissions that permit unauthenticated users to reach SharePoint administrative pages. Users can either provide the URL of a target SharePoint site or a text file containing multiple URLs to SharePoint sites to be tested in bulk. This handy utility also allows users to specify optional HTTP proxy details, as well as HTTP cookie information, thereby making it possible to test admin page access of an authenticated user.
The zip file download contains both the SharePointURLBrute Perl script and a Windows executable version generated from it using Perl2Exe. The zip also contains SharePoint – URL Extensions – 18MAR2012.pdf, a reference document that maps out common SharePoint administrative pages to their respective URL extensions (e.g. “Administration Web Service” -> http://<site>/_vti_bin/Admin.asmx).
Google and Bing Hacking Dictionary Files
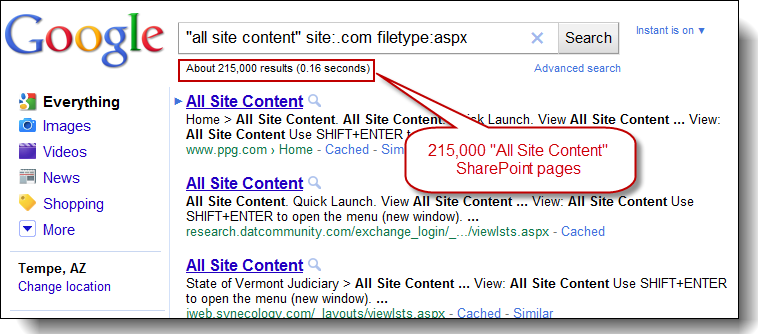
New GoogleDiggity input dictionary file contains 121 queries that allow users to uncover SharePoint specific vulnerabilities exposed via the Google search engine. This dictionary helps assessors locate exposures of common SharePoint administrative pages, web services, and site galleries that an organization typically would not want to be made available to the public, let alone indexed by Google.
It can be imported for use within the SearchDiggity GUI tool from the menu: “File” -> “Import Query Definition”.
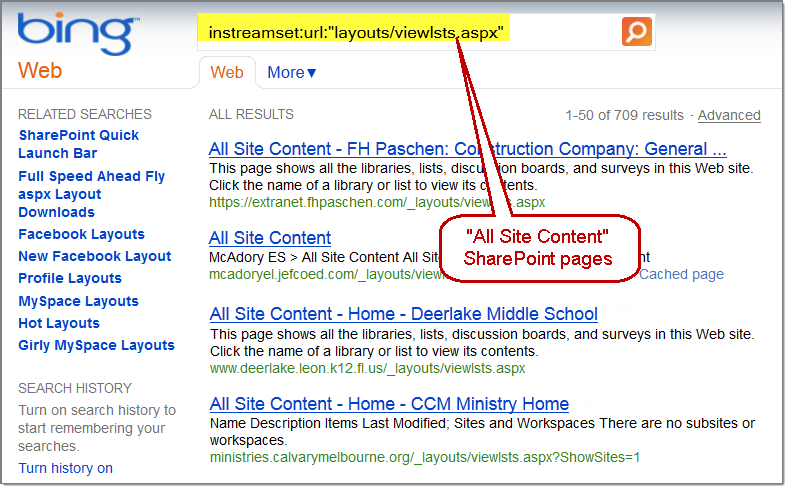
Recently, we’ve also created a Bing hacking dictionary (124 queries) that can be imported into BingDiggity and used to identify SharePoint exposures as well.
SharePoint Hacking Alerts for Google and Bing
SharePoint Hacking Alerts provide real-time vulnerability updates from both the Google and Bing search engines. These convenient RSS feeds help locate exposures of common SharePoint administrative pages, web services, and site galleries that an organization typically would not want to be made available to the public, let alone indexed by Google and Bing.
Google Alerts have been created for all SharePoint related search strings, which generate a new alert each time newly indexed pages by Google match one of those regular expressions. Microsoft Bing’s &format=rss directive was used to turn Bing searches into RSS feeds
SharePoint UserDispEnum
UserDispEnum is a new SharePoint user enumeration tool that exploits insecure access controls to the /_layouts/UserDisp.aspx?ID=1 page. This utility cycles through the integer ID values from 1 onward to identify valid users, account names, and other related profile information that can easily be extracted from the SharePoint user profiles.
For real, live examples of SharePoint site deployments insecurely exposing this functionality to anonymous users on the Internet, see Google results of: “http://www.google.com/#q=inurl:”/_layouts/userdisp.aspx”. Users can leverage Bishop Fox’s GoogleDiggity hacking tools to identify these exposures within their own organization, and then employ the UserDispEnum tool to exploit them during penetration tests.
SharePoint_UserDispEnum_v1.zip will be available soon for download.
SharePoint DLP Tools
COMING SOON – Bishop Fox data loss prevention (DLP) tools for Microsoft SharePoint. SharePoint DLP Tools utilize administrative web services to help automate the searching of SharePoint files and lists for SSNs, credit card numbers, passwords, and other common information disclosures.