You’re a professional. You’re equipped with the latest in elite, customized RFID hacking tools. So, it's high time you put a silencer on your Tastic RFID Thief – the weaponized, long-range badge reader. We’ll show you how to avoid the embarrassingly loud beep when turning on your RFID badge stealer during your next physical penetration test. Because after all, silence is golden.
Silencer for Your Weaponized RFID Reader
So, you’ve built yourself a customized Tastic RFID Thief. Nice work. Fortunately, all the hard work is now done. It’s time for the finishing touches.

The Tastic RFID Thief is a long-range RFID reader that can steal the proximity badge information from an unsuspecting employee as they physically walk near this concealed device. Specifically, it is targeting 125KHz, low frequency RFID badge systems used for physical security, such as those used in HID Prox and Indala Prox products. It can even be used to weaponize a high frequency (13.56MHz) RFID reader, such as the iClass R90 Long Range reader.
There are 2 ways we can silence the HID MaxiProx 5375 commercial badge reader that we used to create the Tastic RFID Thief.
Method 1 – Mostly Silent – Flipping the Beeper’s DIP Switch
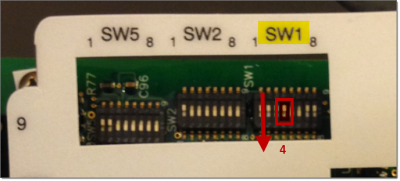
The first method involves simply flipping a single DIP switch, which will render the device silent, except for when it is first turned on. All subsequent badge reads that normally would have caused a loud BEEP, are now silent.
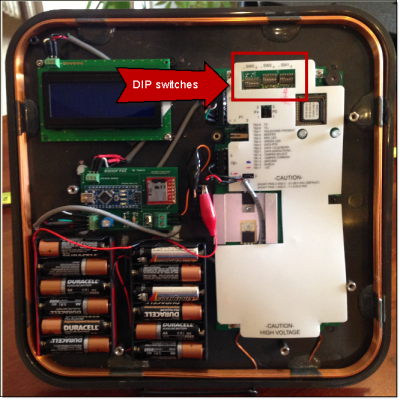
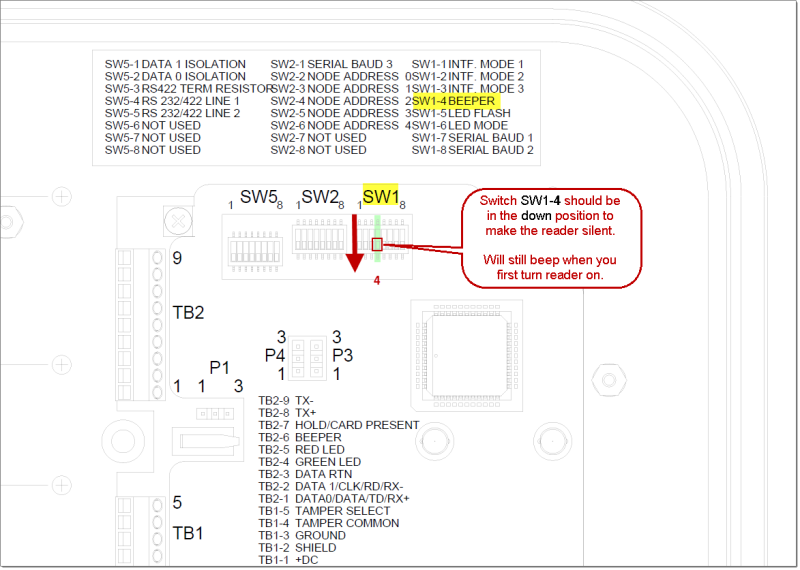
You can find the DIP switch by removing the cover of the Tastic RFID Thief and looking toward the top-right corner. To make the reader mostly silent, flip the SW1-4 switch to the down position.
With this method, you can turn on your Tastic RFID thief in the parking lot (getting the single loud beep out of the way,) and then enter your target facility.
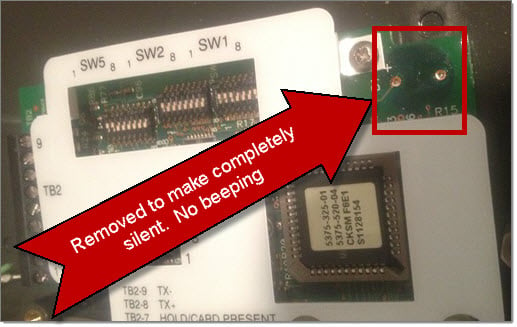
Method 2 – Deadly Silent – Removing the Beeper by Desoldering
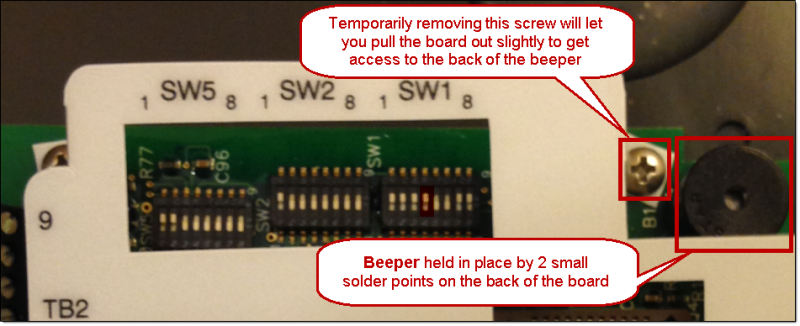
If you are a true professional, you’ll want your RFID hacking equipment completely silent. Fortunately, this is pretty easy to achieve. The actual beeper is a small, circular piece in the top-right corner (to the right of the DIP switches).
By temporarily removing the screw indicated in the image above, you can gently pull the green circuit board out just enough to get behind it and desolder the 2 small solder points holding the beeper onto the device. Alternatively, you can just take a pair of pliers to the small circular beeper and break it off of the board – which isn’t as elegant, but will also work just fine.
In Conclusion
With a couple minor tweaks, you can make your Tastic RFID Thief completely silent. Finally, you’ll have the definitive long-range, silent RFID hacking tool for your physical penetration testing arsenal.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.