
So, most likely you’ve just read the article in USA Today and are wondering what exactly is this “NotInMyBackYard Diggity” tool? What does it do, and how can it help me? Well, you’ve come to the right place.
NotInMyBackYard (NIMBY) - The Gist
According to the Verizon - 2012 Data Breach Investigation Report, in most large organizations notification of a breach occurred when the thief made the disclosure known. They go on to joke about creating “a new breach discovery classification of ‘YouTube,’ ‘PasteBin,’ and ‘Twitter’”. NotInMyBackYardDiggity makes it easy to search for your sensitive information in third-party sites (i.e. “not your backyard”).
This tool leverages both Google and Bing, and comes with pre-built queries that make it easy for users to find sensitive data leaks related to their organizations that exist on 3rd party sites, such as PasteBin, YouTube, and Twitter. Uncover data leaks in documents on popular cloud storage sites like Dropbox, Microsoft SkyDrive, and Google Docs. A must have for organizations that have sensitive data leaks on domains they don’t control or operate.
Another element worth noting is that this tool is not only designed to help large organizations, but also will be an extremely useful tool for individuals to use to sweep the web to see if their personal information is currently be exposed somewhere on the Internet due to some public breach or because some reckless company is playing fast and loose with their data. For example, this tool would have been extremely helpful to the 43,000 Yale alumni who had their personal info exposed via an Excel spreadsheet on a public website.
Getting Up and Running in 3 Easy Steps
NotInMyBackYard Diggity is actually part of our larger search engine hacking tool: SearchDiggity. To get setup and quickly begin discovering where your personal information may be leaked on the Internet, follow these easy steps:
Step 1 - Install the SearchDiggity MSI file
Locate and install the latest version of SearchDiggity. A simple MSI installer file can be found at: Attack Tools - Google Hacking Diggity Project.
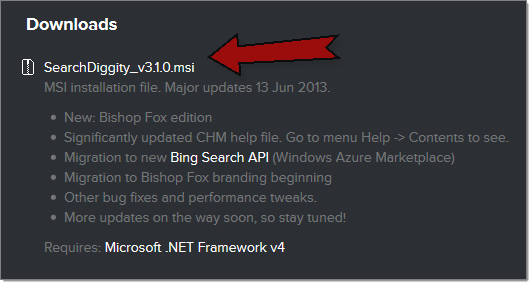
Run through the simple installer wizard (pretty much keep clicking “Next”)
Step 2 - Run SearchDiggity
The installer creates a desktop icon, just double click on it.
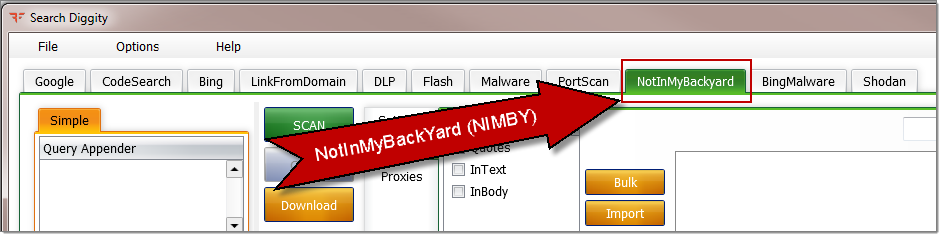
Once open, you’ll find the tab for NotInMyBackYard Diggity over to the right:
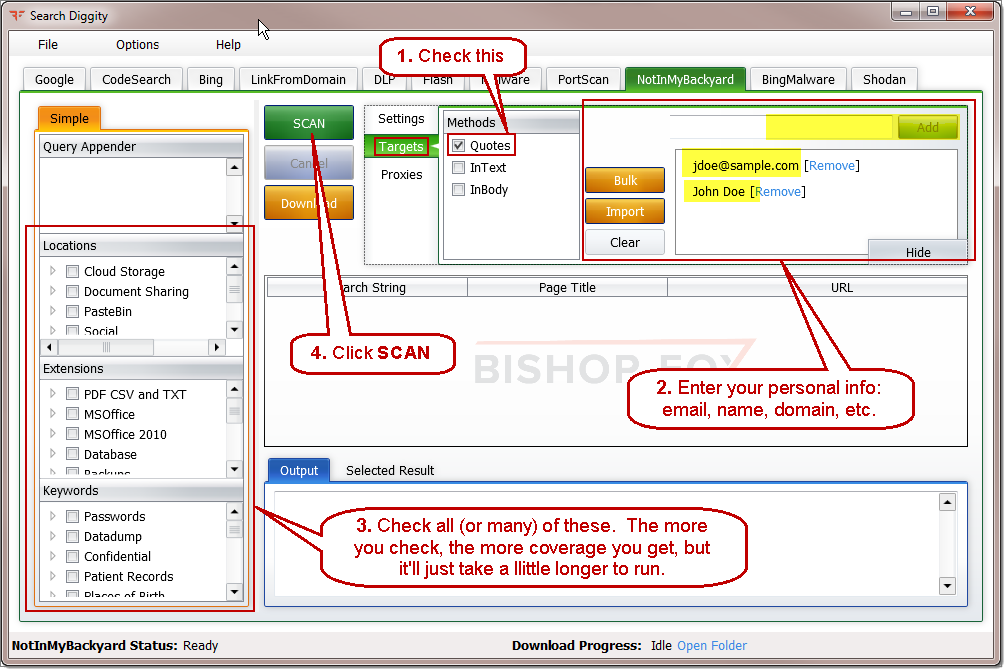
Step 3 - Enter your sensitive info to search for, check the boxes, and click Scan
Ok, so maybe that’s a couple steps. But still pretty simple.
Enter your personal info in Targets (examples: name, email, domain of your company, SSN,…)
Check some boxes and click SCAN.
More details are coming soon for NotInMyBackYard Diggity
More details for NotInMyBackYard will be coming later today in a follow up blog post, but this should get you off and running. Be sure to check out our videos, presentation slides, and project pages for more info on our various search engine hacking tools:

Updates with additional guidance
UPDATED 3 - To answer the most frequently asked question, there is no Mac version of NotInMyBackYard. Its MS Windows only, sorry.
UPDATED 2 - See NotInMyBackYard slides providing more detail on the tool and how it works.
UPDATED 1 - I just created a Diggity Media Gallery and added a YouTube playlist with our various presentations over the past three years to date, interviews, and other useful tutorials that will help new comers get up to speed on the various attack and defense tool in the Diggity search engine hacking arsenal. I will continue to add other tool specific videos, slide decks, and tool screenshot galleries in the near term. Stay tuned.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.



